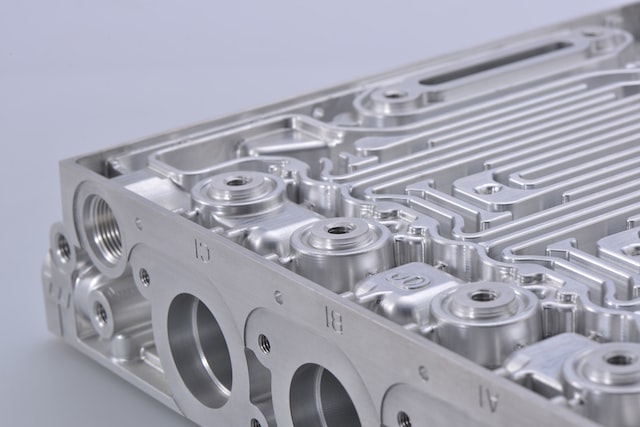
The process of plastic injection molding is highly versatile. While it involves an initial investment in tooling, the cost per part is comparatively low compared to alternative manufacturing processes. It is particularly beneficial for producing intricate plastic parts in large quantities. Additionally, injection molding supports over-molding, whereby a second layer of plastic is molded onto […]
Category: Industry / Tech
Trenchless Pipelining vs. Traditional Methods – Which is Better?
Trenchless pipelining is an innovative method to restore deteriorated pipes. It eliminates the need for extensive digging, saving both homeowners and plumbing companies time and money. The process is also less disruptive, allowing occupants to remain on the property while the work is being performed. This article will compare trenchless pipelining to traditional methods to […]
How to Choose a Reliable Contractor for Oil Tank Installation
An OFTEC registered engineer can self-certify their work and ensure all regulations are met. This will help you avoid fines and faults down the road. Replacing an oil tank isn’t a DIY job. It is a dangerous project and should be handled by professionals. Doing so will save you money and ensure your safety and […]
The Best Practices For Embedding A Large PDF On Your Website
Embedding large PDF files on your website can present challenges in terms of file size, loading times, and user experience. However, by following best practices, you can ensure a smooth and optimized embedding process for large PDFs. In this article, we will explore the best practices for embedding large PDFs on your website, ensuring optimal performance […]
How a Gateway Security Platform Can Protect Your Business From Cyber Attacks
Consider a gateway security platform if you’re looking for a way to protect your business from cyberattacks. These solutions prevent unsecured web traffic from entering your network and analyze it to identify malicious content. These secure gateways include URL filtering, malware detection, and data loss prevention. Some even incorporate sandboxing to block zero-day threats. Detecting […]
What to Look for When Choosing Voice Transcription Software
When choosing voice transcription software, it is important to consider a few things. These include accuracy, ease of use, and convenience. Accuracy is crucial because it will ensure that you receive accurate transcripts. Some programs are more accurate than others, so read reviews before making your final decision. Accuracy When choosing voice transcription software, you […]
How Do Minitec Extrusions Work
MiniTec extrusions are a popular building material for industrial machinery and automation systems. They are strong, lightweight, and corrosion-resistant, making them ideal for many applications. This article will provide an overview of how MiniTec extrusions work and why they are so valuable in a variety of industries. By understanding their design principles and features, users […]
6 Things You Need to Know For Photo Printing
Whether you’re looking to print a photo from a digital file or a photo taken with a camera, there are some things you need to know about the process. These tips will help you make your images look their best before you print them. Aspect Ratio Getting the correct aspect ratio for photo printing can […]
3 Things About Marine Paint Supplies Every Boat Owner Should Know
If you’re considering painting your boat yourself, you need to understand a few things before you start. First, there are different types of paint. For example, Alkyd enamel and Modified epoxy are different. Copolymer ablative antifouling paints are. Alkyd Enamel Alkyd enamel is a traditional oil-based marine paint, and it is one of the easiest to […]
What Does a UX Consultant Do?
A user experience (UX) consultant links the business owner, the software, and the users. They create a design system and test it to ensure the software is usable by the users. Create a Design System Creating a design system is a great way to streamline your workflow. Design systems can help you create a consistent […]